What is Phishing?
Phishing is a psychological attack used by cyber criminals to trick you into giving up information or taking an action. Phishing originally described email attacks that would steal your online username and password. However, the term has evolved and now refers to almost any message-based attack. These attacks begin with a cyber criminal sending messages pretending to be someone you know. There are a wide range of forms this could take, some could pretend to be your friend, your bank, or store.
These messages will entice you into clicking malicious links, opening an infected attachment, or responding to a scam. Cyber criminals craft these good-looking emails and send them to millions of people around the world. The criminals do not know who will fall victim. They simply know that the more emails they send out, the more people they will have the chance to hack. In addition, cyber criminals are not limited to just email but will use other methods, such as instant messaging or social media posts.
What is Spear Phishing?
The concept is the same as phishing, except that the targeted messages are sent to a few people instead of many. With spear fishing, the cyber attackers learn about their targets, by reading the intended victims' LinkedIn or Facebook accounts. They would also read messages they posted on public blogs or forums. Based on this research, the attackers then create a highly customized email that appears relevant to the intended targets. This way, the individuals are far more likely to fall victim.
Why Should I Care?
You may not realize it, but you are a phishing target at work and at home. you and your devices are worth a tremendous amount of money to cyber criminals, and they will do anything they can to hack them. YOU are the most effective way to detect and stop phishing. If you identify an email you think is a phishing attack, call your security team right away. If you are concerned you may have fallen victim, do not hesitate to contact them. To learn more about phishing or to demo the SANS Securing The Human phishing testing platform, please visit Security Awareness Website.
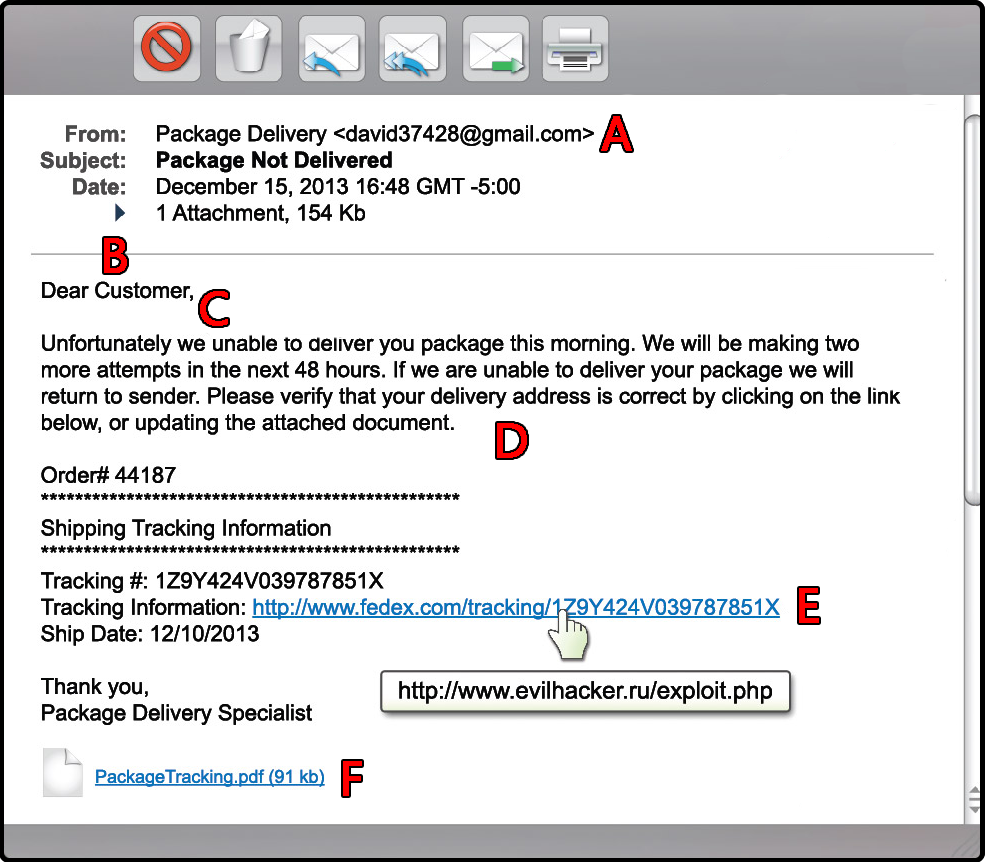
Phishing Indicators
- Check the email addresses. See if the "FROM" address is someone's personal account. If email address reads @gmail.com or @hotmail.com it is most likely an attack. Also, check the "TO" and "CC" fields. Is the email being sent to people you do not know or do not work with?
- Be suspicious of emails addressed to "Dear Customer" or that use other generic salutation. If a trusted organization has a need to contact you, they should know your name and information. Also ask yourself, am I expecting an email from this company?
- Be suspicious of grammar or spelling mistakes; most businesses proofread their messages carefully before sending them.
- Be suspicious of any email that requires "immediate action" or creates a sense of urgency. This is a common technique to rush people into making a mistake. Also, legitimate organizations will not ask you for your personal information.
- Be careful with links, and only click on those that you are expecting. Also, hover your mouse over the link. This shows you the true destination of where you would go if you clicked on it. If the true destination is different that what is shown on the email, this is an indication of an attack.
- Be suspicious of attachments. Only click on those you are expecting
- Be suspicious of any message that sounds too good to be true. No, you did not just win the lottery.
- Just because you got an email from your friend does not mean they sent it. Your friend's computer may have been infected or their account may be compromised. If you get a suspicious email from a trusted friend or colleague, call them on the phone.
Other Indicators:
- May contain fuzzy logo symbols, which are not genuine
- May not contain email signatures or any contact information
- May contain bad grammar and capitalized letter errors
- Generally require you to take quick action, such as verifying your account to prevent it from being deactivated
- Be particularly vigilant during holidays or during significant events since attackers heighten their activity during these times.
What to do if you get a phishing email?
Send any phishing emails you receive, including its full header information, to the Fredonia Information Security Office.
- If you suspect it may be a phishing email, Fredonia ISO can review the message and advise if it is legitimate or not.
- Never respond to any email with confidential information. Fredonia and other legitimate businesses will never ask for this information via email.
- Use your mouse to hover over links in an email. This will show you the actual website you will be directed to if you click on the link. It is always best to type the address yourself into your web browser, rather than clicking a link in an email.
What should I do if I clicked on a link, opened an attachment or provided information via a phishing email?
- Email the Fredonia ITS Center immediate or call 716-673-3407.
- If you entered your password, change it right away.
- Check your anti virus software or computer security if you click a link but did not enter your password
- Depending on the type of phishing attempt, you may need to check you other online accounts (e.g. financial etc.).
How to you protect yourself?
- Beware of messages that claim your account has been suspended
- Be suspicious of any email containing urgent requests for personal financial information
- Never click on a link in an email. Instead, always type the legitimate Web address of the site you want to reach directly into your Web browser.
- Be suspicious of email messages and other electronic communications from sources you do not know or recognize
- Use the latest versions of your operating system (OS) and applications
- Have the latest security software updates (patches) installed. This includes patches for your OS and applications
- Keep your anti-virus software up to date
- Report any suspicious emails
- Avoid and report phishing emails in Google
Related articles